Snapshots
Database snapshots provide a point-in-time view of a database's store. In Sui, the database snapshot captures a running database's view of the Sui network from a particular node at the end of an epoch. While validators can enable snapshots, they are typically most valuable for Full node operators.
Snapshots of the Sui network enable Full node operators a way to bootstrap a Full node without having to execute all the transactions that occurred after genesis. You can upload snapshots to remote object stores like S3, Google Cloud Storage, Azure Blob Storage, and similar services. These services typically run the export process in the background so there is no degradation in performance for your Full node. With snapshots stored in the cloud, you're more easily able to recover quickly from catastrophic failures in your system or hardware.
To maintain a healthy Sui network, Sui encourages the Sui community to bring up additional snapshots to ensure stronger data availability across the network.
Supported snapshot types
Sui supports two types of snapshots:
- RocksDB snapshots are a point-in-time view of a database store. This means that the snapshot keeps the state of the system at the moment it generates the snapshot, including non-pruned data, additional indices, and other data.
- Formal snapshots are database agnostic with a minimalistic format, in other words they contain only the data necessary to restore a node to a valid state at the specified epoch, thus they have a much smaller storage footprint and are generally faster to restore from when compared to database snapshots. Formal snapshots are also supported natively by the Sui protocol. In this context, this means that we can cryptographically verify the contents of the formal snapshot against a commitment from the committee at the epoch we are restoring to. This verification happens automatically and by default during a Formal snapshot restore (unless explicitly bypassed).
Formal snapshots are not suitable for use if you are running an RPC node that does any historical data lookups. For more information on node data management, see Data Management.
You can configure a Full node snapshot to generate a state snapshot at the end of each epoch. A single Full node can generate RocksDB snapshots, Formal snapshots, or both.
Enabling snapshots
Full nodes do not take snapshots by default. To enable this feature you must apply specific configs to your Full node.
Follow these steps to change the configs for a Full node:
- Stop your node, if it's running.
- Open your fullnode.yaml config file and apply config updates as the following sections show.
- Save the fullnode.yaml file and restart the node.
Enabling RocksDB snapshots
Add an entry to the config file for db-checkpoint-config. Using Amazon's S3 service as an example:
db-checkpoint-config:
perform-db-checkpoints-at-epoch-end: true
perform-index-db-checkpoints-at-epoch-end: true
object-store-config:
object-store: "S3"
bucket: "<BUCKET-NAME>"
aws-access-key-id: “<ACCESS-KEY>”
aws-secret-access-key: “<SHARED-KEY>”
aws-region: "<BUCKET-REGION>"
object-store-connection-limit: 20
object-store: The remote object store to upload snapshots. Set as Amazon'sS3service in the example.bucket: The S3 bucket name to store the snapshots.aws-access-key-idandaws-secret-access-key: AWS authentication information with write access to the bucket.aws-region: Region where bucket exists.object-store-connection-limit: Number of simultaneous connections to the object store.
Enabling Formal snapshots
Add an entry to the config file for db-checkpoint-config. Using Amazon's S3 service as an example:
state-snapshot-write-config:
object-store-config:
object-store: "S3"
bucket: "<BUCKET-NAME>"
aws-access-key-id: “<ACCESS-KEY>”
aws-secret-access-key: “<SHARED-KEY>”
aws-region: "<BUCKET-REGION>"
object-store-connection-limit: 200
The configuration settings shown in the example are specific to AWS S3, but GCS, Azure Storage, and Cloudflare R2 are all supported.
Restoring a Full node using snapshots
Restoring using RocksDB snapshots
To restore from a RocksDB snapshot, follow these steps:
Download the snapshot for the epoch you want to restore to your local disk. There is one snapshot per epoch in s3 bucket.
Place the snapshot into the directory that the
db-configvalue points to in your fullnode.yaml file. For example, if thedb-configvalue points to/opt/sui/db/authorities_db/full_node_dband you want to restore from epoch 10, then copy the snapshot to the directory with this command:aws s3 cp s3://<BUCKET_NAME>/epoch_10 /opt/sui/db/authorities_db/full_node_db/live --recursive.Use
--no-sign-requestto bypass setting AWS credentials for the CLI.Make sure you update the ownership of the downloaded directory to the sui user (whichever linux user you run
sui-nodeas)sudo chown -R sui:sui /opt/sui/db/authorities_db/full_node_db/live.Start the Sui node.
When you restore a Full node from a snapshot, write it to the path /opt/sui/db/authorities_db/full_node_db/live. To restore a Validator node, use the path /opt/sui/db/authorities_db/live.
Restoring using Formal snapshots
To restore using a Formal snapshot, use the sui-tool binary. sui-tool can be downloaded along with other sui binaries.
See Install Sui for more details.
The following steps can be used to restore a node from a Formal snapshot:
- If it's running, stop the node.
- Run the command:
sui-tool download-db-snapshot --epoch "<EPOCH-NUMBER>" --genesis "<PATH-TO-GENESIS-BLOB>" \
--formal --network <NETWORK> --snapshot-bucket <BUCKET-NAME> --snapshot-bucket-type <TYPE> --path <PATH-TO-NODE-DB> --num-parallel-downloads 50 --no-sign-request --snapshot-bucket-type=s3--epoch: The epoch that you want to download, for example200. Mysten Labs hosted buckets will only keep the last 90 epochs.--genesis: The path to the location of the network'sgenesis.blob.--formal: If set, restore from formal (slim, DB agnostic) snapshot.--network: Network to download snapshot for. Defaults to "mainnet".--snapshot-bucket: Source snapshot bucket name, egmysten-mainnet-snapshots.--snapshot-bucket-type: Snapshot bucket type. GCS and S3 currently supported.--path: Path to snapshot directory on local filesystem.--no-sign-request: If true, no authentication is needed for snapshot restores.
Mysten Labs managed snapshots
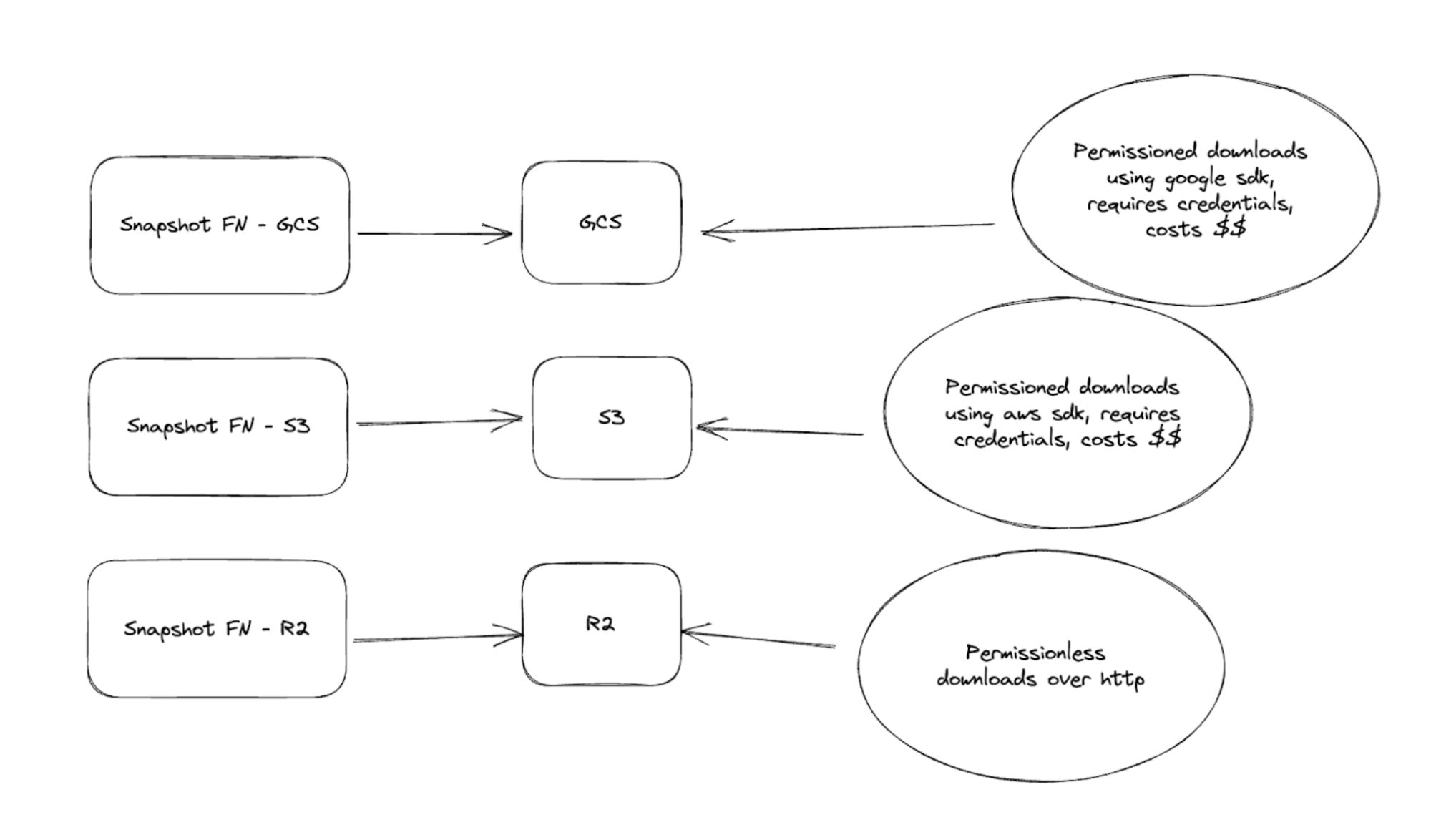
Mysten Labs hosts two tiers of snapshot storage access. High throughput, Requester Pays enabled buckets, and free, permissionless buckets.
High throughput, Requester Pays enabled buckets:
- GCS and S3 are both setup with requester pays. This means that you'll need to provide a set of valid AWS/GCP credentials when downloading from these buckets. Requester Pays means you are charged for the egress costs of pulling the snapshot data.
- If you are looking for the best download speeds, we recommend using the S3 buckets with transfer acceleration enabled.
Free, permissionless buckets:
- These are currently hosted on Cloudflare R2, currently only in North America, but we plan on adding more regions soon.
- Since the bucket is open to the internet, there's no need to provide any cloud credentials.
Bucket Names
S3
Testnet: s3://mysten-testnet-snapshots/, s3://mysten-testnet-formal/
Mainnet: s3://mysten-mainnet-snapshots/, s3://mysten-mainnet-formal/
GCS
Testnet: gs://mysten-testnet-snapshots/, gs://mysten-testnet-formal/
Mainnet: gs://mysten-mainnet-snapshots/, gs://mysten-mainnet-formal/